What is cryptography?
Cryptography is the study of techniques based on mathematical problems difficult to solve, in order to ensure the security (confidentiality, integrity, authenticity) of data. Cryptanalysis is the study of mathematical techniques for attacking cryptographic techniques or security services, and cryptology is the combination of cryptography and cryptanalysis in a single discipline.
Application of cryptography is encryption. Encryption is the transformation of data into a format that is impossible to read without knowing the correct bit sequence. The bit sequence is called a “key” and is used in conjunction with an appropriate algorithm / function. The reverse process is decryption and requires knowledge of the key. The purpose of encryption is to ensure the confidentiality of data by keeping it secret from anyone who has access to it.
Types of Cryptography
Asymmetric Cryptography
Asymmetric cryptography (Public Key Cryptography) uses two different keys for encryption and decryption. Each user has a pair of keys, one is called a public key and the other is called a private key. The public key is made public, while the private key is always kept secret. The private key is never transmitted over the network and all communications are based on the public key. The need for the sender and recipient to share the same key disappears along with many problems that we will see below.
The only requirement of asymmetric cryptography is the accredited and confirmed association of public keys with their holders, so that intentional or unintentional impersonation is not possible. Asymmetric encryption can be used not only for encryption, but also for the production of digital signatures.
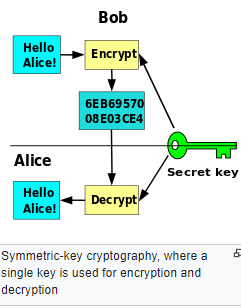
Symmetric Cryptography
In Symmetric Cryptography or Secret -Key Cryptography, the sender and recipient of a message know and use the same secret key. The sender uses the secret key to encrypt the message and the recipient uses the same key to decrypt the message. This method is called symmetric cryptography or secret key cryptography. Symmetric cryptography is used not only for encryption, but also for authentication.
What is E2E encryption?
End-to-end encryption is an asymmetric encryption application. As the name implies, end-to-end encryption protects the data so that it can only be read at both ends, by the sender and the recipient. No one else can read the encrypted data, including hackers, governments and even the server through which the data passes. End-to-end encryption inherently involves many important things.
What is Backdoor?
A backdoor may take the form of a hidden part of a program, a separate program, code in the firmware of the hardware, or parts of an operating system such as Windows. Backdoor for some cases called as vulnerability because it is used by intruders(hackers) to enter a system or an application.
Default passwords (or other default credentials) can function as backdoors if they are not changed by the user. Some debugging features can also act as backdoors if they are not removed in the release version.
European Union and E2E Encryption
So, we know that end-to-end encryption in its best configuration makes it impossible to eavesdrop. It is better in terms of digital security of user privacy. But if we have a back door to an application, things change in terms of privacy and security. It is certain that in such a case the end-to-end encryption weakens in terms of its violation and becomes less secure than any malicious intruder.
It is true that the effectiveness of end-to-end encryption has been discussed in the European Union. The resolution design does not require backdoor for applications, nor does it prohibit end-to-end encryption.
It is essentially about accessing electronic evidence to effectively fight terrorism, organized crime, child sexual abuse and a host of other cyber criminals. This access is essential for the success of law enforcement and criminal justice in cyberspace. However, there are cases where encryption makes accessing and analysing evidence extremely difficult or impossible in practice, as in many cases end-to-end encryption.
In conclusion, the EU seeks to start an active debate with the technology industry and with the close involvement of research, academia, industry, civil society and other stakeholders, in order to strike the right balance between ensuring the continued use of strong encryption technology and law enforcement and the judiciary to operate on the same terms as in the offline world. Possible technical solutions should respect privacy and fundamental rights and maintain the value that technological progress offers to society.




