There is a cyber threat, that is bringing many companies to their knees in recent times and providing criminals with large and easy profits. The number one danger for managers and employees is ransomware, a malware that exploits vulnerabilities in security systems to steal data. It is an effective way to take possession of a device and prevent the owner from accessing it. A standard, repetitive pattern that allows hackers to demand a ransom to be paid, which for the attacker is the only way to regain possession of the locked and unavailable information.
In recent weeks, ransomware has grabbed the headlines worldwide for two high-profile cases. The first was a hacker group known as REvil, which targeted Quanta Computer, a Taiwanese company that is the largest manufacturer of laptops and has companies such as HP, Dell, Sharp, Google, Facebook and Apple among its customers. The criminals’ offensive was aimed at Apple, with the hackers obtaining several confidential documents (several GB of data) relating to products that the Cupertino-based company will unveil in the coming months. The material in question included numerous drawings and detailed information on the Apple Watch (manufactured by Quanta Computer itself), MacBook Air and MacBook Pro.
With the threat of being able to reveal trade secrets, which are vital for any technology company and even more so for Apple given its history and the enormous attention it pays to security and its ability to keep its projects secret, REvil demanded a $50 million ransom from Quanta Computer and then Apple itself, setting a deadline of 1 May, and then postponing the deadline by a week.
In order to demonstrate their strength and the credibility of the demand, the hackers spread more than 20 images on the dark web of potential future MacBooks, which will come onto the market later this year. Despite this, the two companies decided not to pay, forcing the criminals to backtrack and lower their demands, reducing the ransom to $20 million, to be paid in cryptocurrency. The latest news released on the issue, however, indicates ongoing negotiations between REvil and Quanta, with the publication of a screenshot of an alleged chat between the two parties.
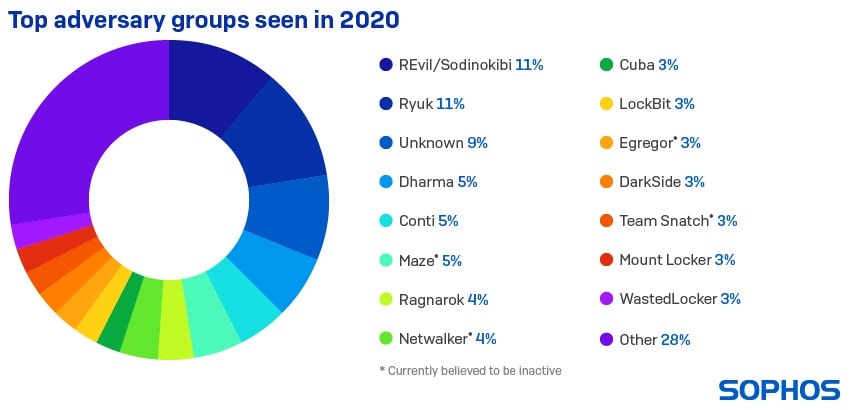
One of the most dangerous ransomware
Active since 2019, the group behind the acronym Ransomware Evil, also known as Sodinokibi, has attracted cybersecurity experts due to the mix of malware complexity and effectiveness. According to Kaspersky’s research, it is one of the top five most dangerous ransomware out there, affecting nearly 20 different industries: Engineering & Manufacturing (30%), Finance (14%), Professional & Consumer Services (9%), Legal (7%), and IT & Telecommunications (7%). The rise is evidenced by the numbers, specifically the more than 160 targets hacked and the steady increase in ransom demands. The highest amount ever advanced among known operations is signed REvil: 50 million dollars was the ransom in Monroe (XMR), another cryptocurrency, demanded last March by Acer, whose protection system was breached through a Microsoft Exchange flaw. The Taipei-based company has maintained absolute secrecy about the breach, without denying a “suboptimal situation”.
The other case that held the US in check for days was the computer attack that blocked one of the most important American oil pipelines. It was Colonial Pipeline, a company that controls the supply of almost half of the eastern seaboard, that was put under attack, causing problems for many petrol pumps in 15 states. Although the breach was confined to the company’s corporate network, with the company deciding to stop supplying fuel to avoid the possibility of the threat spreading to the security system on which distributors and suppliers depend, after five days of difficulty and uncertainty over the short-term future, Colonial Pipeline chose to pay the ransom set by DarkSide.
The hacker group also made amends for the inconvenience created, specifying that they were not pursuing political interests, as their only goal was always to collect money. Joseph Blount, the company’s CEO, confirmed the payment in bitcoins, which at the time of the transaction amounted to around $4.4 million. In an interview with the Wall Street Journal, he explained that the decision to pay the ransom was due to the impossibility of establishing the severity of the problem and, therefore, the number of days that the plants would have to be shut down.
The average cost of recovering data after a ransomware attack has more than doubled in the last 12 months
The spread of ransomware to major companies and infrastructures is linked to the increase in the number of incidents and revenue that this type of operation provides too cybercriminals. According to the state of Ransomware 2021 published by online security firm Sophos, the average ransomware attack costs $1.85 million, double the $761,106 it cost last year to pay the ransom and get all your data back. The average payment is $170,404, but research involving 5400 managers from medium-sized IT companies in 30 countries shows that only 8% of companies have recovered the stolen information, while 29% have less than half of their data back.
The good news is that the number of companies that have suffered a ransomware attack has decreased from 51% to 37% in the last 12 months, but this figure is downgraded by a different approach of cyber criminals. “We have seen a shift from large-scale, generic, automated attacks to more targeted attacks that exploit hands-on-keyboard hacking. As a result, although the overall number of attacks is lower, the damage potential of this type of attack is much higher and business recovery is much more complex,” explains Chester Wisniewski, principal research scientist at Sophos.
To understand how criminals have been able to secure much larger ransom sums in the past couple of years, we need to look at the evolution of ransomware. While the goal used to be to encrypt data to get the money and release the key to decrypt the files, datas now stolen with the promise of disclosure if the money is not paid. This has changed the relationship between the parties, as companies risk having their business secrets published.
In this way, hackers have come to focus their attack on data theft and extortion, and have not bothered to encrypt the files. This mechanism has complicated the problem for companies, particularly those with large databases of personal customer information, who are more likely to pay ransoms to avoid breaches, or at least the possibility that the attack they have suffered will not be released to the public by cybercriminals.



