Microsoft takes on 2021 cyber threats.
With the end of the year 2021, if we take a look back on what it’s left behind, we can witness that cybercrimes have become more and more sophisticated. Cyber attacks for this past year have had a large spread in different working areas, such as information technology, infrastructure, health care systems, financial services etc. Alongside with these new relentless cyber crimes, we can also see that new and different measures are taking place and being implemented in order to reduce the risks coming from all directions. Governments are passing new laws in order to avoid new upcoming risks that seem that are always on the rise, from one year to another. Along with the government, changes in policies are being made in large software companies that offer services worldwide, such as Microsoft.
Based on the latest digital defense report published by Microsoft on October 2021, the most common cyber-attacks were ransomware, malicious emails, file inclusion malwares and much more.
Insights from Microsoft Digital Defense Report 2021 – a look back on 2021
According to Microsoft’s digital defense report of 2021, ransomware held number one as one of the most common cyber security attacks happening around the world. This type of attack has been desirable by lots of criminals, because it is seen as one low investment, high profit business model that has immediate results.
Ransomware is becoming a modular system like any other big business, including ransomware as a service (RaaS). With RaaS there isn’t a single individual behind a ransomware attack; rather, there are multiple groups. For example, one threat actor may develop and deploy malware that gives one attacker access to a certain category of victims; whereas, a different actor may merely deploy malware. It’s effectively a crime syndicate where each member is paid for a particular expertise. The common payment that has been circulating recently as a form of ransom is through crypto currencies, so that the attackers may remain anonymous throughout the whole transaction.
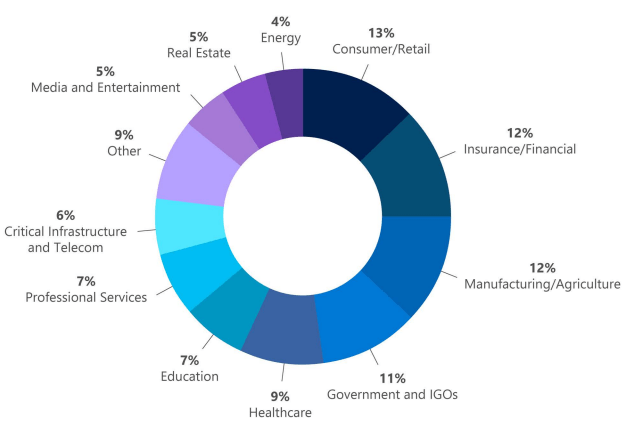
In the graph below it is shown the impact of ransomware attacks in different industries for the last year.
Phishing attacks are being doubled
Reports show that phishing attacks with credential phishing used in many attacks, have been doubled for the past year, which makes this type of attack one of the most common forms of cyber-attacks encountered for 2021. All industries receive phishing emails with some verticals more heavily targeted depending on attacker objectives, availability of leaked email addresses, or current events regarding specific sectors and industries.
“In 2020, the industry saw a surge of phishing campaigns that has remained steady throughout 2021. Internally at Microsoft, we saw an increase in overall number of phishing emails, a downward trend in emails containing malware, and a rise in voice phishing (or vishing).”—2021 Microsoft Digital Defense Report
Different malwares rising
With the growth of phishing attacks, different malwares have been spread along, which caused a rise in the numbers globally. Forms of malware that have been shared amongst users mostly have been web malicious scripts, data exfiltration, credential theft etc.
“In every month from August 2020 to January 2021, we registered an average of 140,000 web shell threats on servers, which was almost double the 77,000 monthly average. Throughout 2021 we saw an even bigger increase, with an average of 180,000 encounters per month.”—2021 Microsoft Digital Defense Report
Also popular is a malware that attempts to rename or inject payloads to copy system processes and collect data from browser caches.
(All of these attacks can be found more detailed in the full Microsoft’s digital defense report of 2021.)
But after all these scary attacks that we have witnessed, Microsoft managed to come up with some amazing measures to ensure that attacks like this are being avoided at all costs, or even better predicted since the very beginning.
Microsoft latest tactics to ensure corporate safety- Machine Learning prediction system
One of the latest measures that Microsoft is developing is creating a new prediction method through the use of Machine Learning, to come up with ways on how to avoid different cyber attacks from happening at all. They are gathering different targeted or affected systems, in order to create a system behavior module, to understand a little bit better the nature of these attacks, and what is causing them.
The software giant has used for the past months massive data collected on threat actors through its endpoint and cloud security products, to create a large ML model that can associate a series of tactics, techniques and procedures (TTPs) — the signals defenders can accumulate from an ongoing cyber attack.
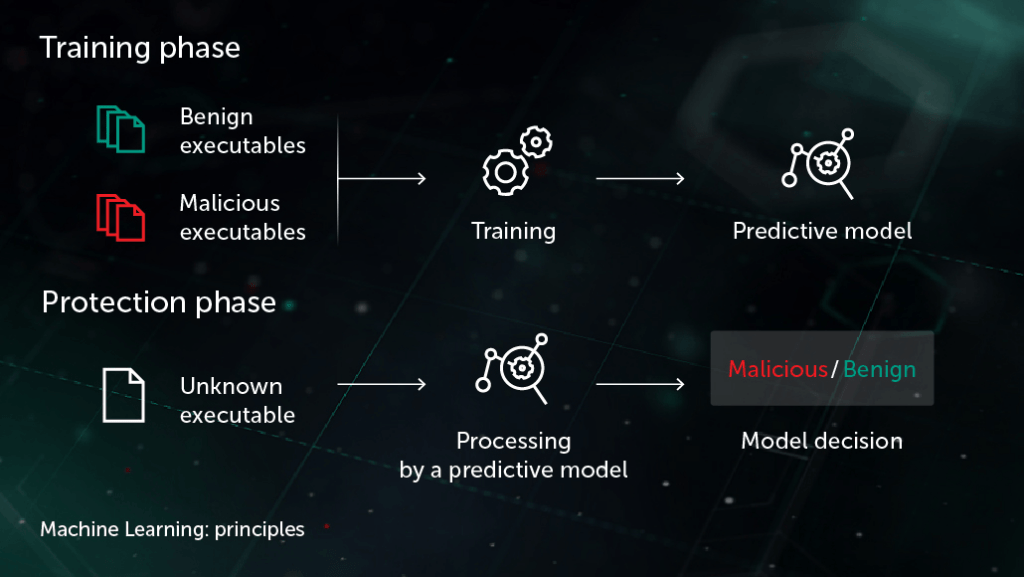
“We are still in the early stages of realizing the value of this approach, yet we already have had much success, especially in detecting and informing customers about human-operated attacks, which are some of the most prevalent and impactful threats today,” the company wrote.
But even with the implementation of ML to make predictions, yet again some challenges remain. These types of models require a lot of specific and correct data on threat actors in order to provide best solutions based on the system behavior. Unfortunately, cyber-attacks vary from their nature of attacking and how they are processed, therefore the recreation of the attacks and predictions of the system behavior are difficult to be made.
But even with the ongoing predictions of the ML model, Microsoft has a nonstop functional service that offers to ensure its clients to achieve greater safety, such as cloud technology.
But even though cloud technology has made a breakthrough in the tech world, is it all you need in order to be safe online?
Cloud computing is nowadays a go-to service, which provides the latest features to ensure safer actions are undertaken. But this technology has yet again proved to be lacking is some areas.
As organizations around the world turn to the cloud, the impact of a massive cloud failure is keeping IT managers awake at night. If a major cloud service provider suffers a set downtime, the damage inflicted on its clients could generate catastrophic financial losses.
Also it is a fact that there are multiple ways on how to attack a cloud service provider, and one of the most common ways is DDOS attack, which is an attack designed to descend resources or systems unavailable to users, by bombarding it with excessive traffic via botnets.
In conclusion, we can see that with the increase of the reliance of the IT services come along the vulnerabilities from cyber attacks. Despite all benefits that are being offered, such as ML predictions to cloud safety, we understand that there is no such thing as fully secure software. Therefore organizations must be aware of these attacks that float around, in the search of their new victim, and what can be done to avoid them at all costs.



