Everybody by now has come across the IoT term in technology. We are witnessing that this technology is emerging and evolving rapidly. Everyone wants to get their hands on it. So, what is IoT and why it has taken the market by its wing?
When we talk about IoT (Internet of Things) we must know that IoT is a set of interconnected devices that exchange data over the network. An IoT system can be established within homes, officers, and even cities. Although IoT is being adopted by different industries and businesses, there are multiple challenges in its adoption. Many governments and companies have woken up to the realization that IoT is becoming a part of every civilian’s everyday existence. Across the globe, security regulations are being created so that data privacy and security can be ensured.
4imag had the opportunity to interview Rob van Kranenburg, the founder of IoT council (an IoT community), author of several books written about IoT technology, and the Chief Innovation Officer of asvin.io. A company that has designed and developed a secure platform to keep safe Industry IoT (IIoT) devices from cyber-attacks. We interviewed Rob regarding IoT, who can help us get a clear view of this emerging technology.
Why did you start the IoT council? What’s the background story on the creation of this council?
“I started the IoT Council with an event in Brussels in 2009 inviting hackers and activists, industry, designers, and policy makers. They all came and joined in workshops together. Since then, people joined a mailing list that is still active. Experts exchange information and meet each other for projects. I wanted to have all opposite positions together in one room as I had realized early that this IoT would not go away, would only grow, and would need a joint vision of people against and people for this kind of total connectivity.”

We would like to ask about your book “The Internet of People for a Post-Oil World”. Can you give us a little more information about your book (a short briefing)? In your book, you talk about transforming the IoT into the internet of people. What do you mean by this statement?
“The book is a conversation between me and Christian Nold. We are old friends, and both have our origins in thinking and literature around self-organization. The arguments we make there are based on the fact that the gaze of the computer is already based on a simplification of life and human activity. It begins its ‘thinking’ based on 3D modeled charts and simplified schedules. We have to make its input more granular, more complicated and messier so that it starts to resemble the roundedness of human life. So we have to slow its progress. That it is able to make when left to its own devices and work on a better understanding of us that the digital gaze should have. That is why AI is so important.”
For anyone interested, the book can be found at this link here
Where do you see the IoT is going? Based on your experience and knowledge of IoT, what are your opinions on the future of the IoT? What is there to be expected to happen in the near future?
“IoT has its own internal mechanisms. Like software ate the world, IoT eats the planet (and its space). There is no logical endpoint in IoT, there is always something left to be added, to be connected. There never is a reason why it should not be connected. As a result IoT will fulfill its logical course, to bring any object, device, animal, plant, human into a large intranet. Also possible creating such a good atmosphere between them that these become interoperable and become one giant library.”
Since IoT is evolving rapidly, and with this enormous digital transformation, alongside come different risks with it. What are some risks that threaten IoT technology?
“To the operation of IoT itself there is no internal risk, it just moves on and does what it does. There is no way to exist outside of IoT business-wise. There were some internal disputes about privacy and security or companies getting too powerful. Yet for the current and next generation’s connectivity is so interwoven with their everyday life. It is no longer distinguishable and everything becomes a tradeoff in terms of convenience.”

Asvin’s Focal Points
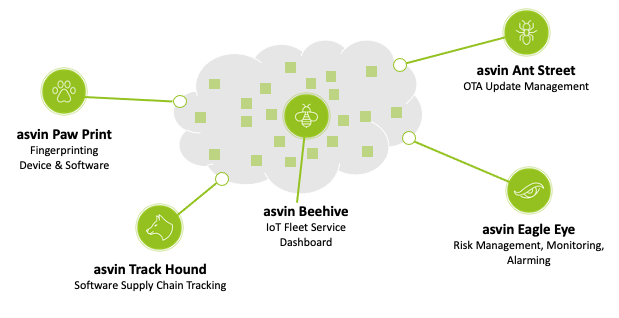
As the CIO of asvin, an innovative company focused on ensuring cyber safety on IoT technology implemented in different fields. Can you please tell to our readers some innovative approaches that asvin is following to ensure cyber safety for the IoT devices (and not only)?
“We try to build the best possible balance between explicit and implicit trust mechanisms. Furthermore, in the world of SCA (Software Component Analysis) key criteria for cybersecurity solutions include vulnerability identification, license risk management, software bill of materials, policy management, SDLC integration, remediation, reporting, and breadth of coverage. Forrester Research scores companies in this field on these eight criteria:
Vulnerability identification 22%
License risk management 13%
Softthware Bill of Materials 10%
Policy Management 10%
SDLC Integration 10%
Remediation 25%
Reporting 5%
Breadth of coverage 5%
This is where you build explicit trust by scoring on these criteria. Balancing operational efficiency with explicit trust mechanisms needs to have a definition of implicit trust that can be operationalized as well. Implicit trust needs a framework – balancing convenience, workload, and operational process with access controls, explicit trust criteria and a broad threat landscape that is proactive and considers emerging threats. Asvin.io aims to be part of a select leading group of SCA who go beyond explicit trust mechanisms to set the standard for supply chain security.
One of Asvin’s focal points is Distrusted Software Bill of Materials, a novel approach to managing supply chain security challenges. By use of Blockchain technologies, an ecosystem of suppliers can commit and exchange information on software used in connected components. The process of commitment is secured by blockchain protocols, and the information stored is trusted by the census mechanism. Information will be additionally stored by encryption methods for distributed computing to avoid unauthorized access to security and IP-relevant information. By that, the entire software supplier ecosystem can easily commit information about the software in use of specific components and define the security and access level of information shared with other suppliers and the OEM.”

Safety, Privacy and Cybersecurity
Based on practices/methodologies that asvin follows to ensure the security of different IoT devices, when do you think we can say we have reached a satisfying level of security?
“In an internet environment, you can only talk about probabilities. TCP/IP – the protocol that runs the internet there is ‘a pass on the packet’, there is no ‘security’ built-in. Security always will be a dynamic relation, you are never fully ‘secure’ or ‘safe’, you can only be ready for the next challenge, that is why readiness is more of a metric. Then reaching a satisfying level of security as you do not know where the next attack will come from.”
Talking about safety, privacy and cyber security, what are your thoughts on the zero-trust approach that seems to be implemented a lot lately by different companies? Do you think that Zero Trust is being implemented correctly? What would you do differently to ensure that a company is embracing in the right way the Zero Trust concept?
“Zero Trust is a relatively new paradigm. It describes a situation that is tuned to the Internet of Things. Things being connected through various protocols, with different security settings. In addition, people working from home, bringing their own devices to work using various cloud operators and networks under a continuous ransomware attack. In this hybrid operation, security needs to be operationalized at different levels of access and at random moments in time the status of anyone in the network can be questioned.
Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of digital interaction. Rooted in the principle of “never trust, always verify,” Zero Trust was created based on the realization that traditional security models operate on the outdated assumption that everything inside an organization’s network should be implicitly trusted. This implicit trust means that once on the network, users – including threat actors and malicious insiders – are free to move laterally and access or exhilarate sensitive data due to a lack of granular security controls. Yet, Zero Trust is not an all-encompassing solution. It is only one piece of the puzzle in bringing the best possible balance between explicit and implicit trust mechanisms.”
It seems that cyber security is one of the main points of focus of technological companies nowadays. What are your thoughts based on this situation? Do you think that companies are following the right approaches towards cyber security and what could be done differently to reach a more cyber-safe environment?
“I suggest public bodies could do more. In this text, The Cybersecurity Aspects of New Entities Need a Cybernetic, Holistic Perspective we propose that every time a device gets approved for an electric license to operate, a cybersecurity check is done as well. If it does not pass certain standards nor comes with some educational note for end-users to install it securely and keep it safe, it does not get to operate in the EU.”
Finally, we are very curious to know about the IoT day, an IoT community. Please give us a little information about this community and the events that are hosted by it. Also, we want to know a bit more about the webinar that will be held on the 9th of April: The state of the art of IoT that you will present alongside Alicia Asin, Lorna Goulden and Mirko Ross. Can you please tell us a bit more about this webinar?
“On the IoTDay community, that is a group of engineers and researchers who do care about the quality of their products and services and the real relationship with citizens. That is why over 500 events have been held in the last twelve years, self-organized and mainly informal in nature.
For the webinar, come and listen! The link of the event can be found HERE. “



