XM Cyber: With the rise of different cyberattacks, businesses worldwide have become more cautious about the measures they want to undertake to ensure excellent safety. But what we are witnessing in many different scenarios is that these cyber solutions that companies are trying to implement often don’t cover every aspect of a complicated cyberattack to take it down completely. Attackers have become more sophisticated in their intrusive methods. Therefore the approaches needed to face these threats need to be proactive. A common strategy that everyone should follow is to anticipate risk, analyze every single scenario beforehand, and proceed with caution by enabling all the best measures to increase security in information systems. And of course, this strategy requires a lot of effort from cybersecurity (threat assessments) teams.
Fortunately, a new and innovative company is changing threat prediction and analysis by creating a proactive approach in the cyber defense world. Named a leading hybrid cloud security company in today’s market, XM Cyber is changing how innovative organizations approach cyber risk. XM Cyber has created an exciting platform called Attack Path Management Platform, which can help its users to predict threats by simulating attacks and stopping them from happening in the first place. We at 4imag had the opportunity to discuss with the XM Cyber team, where we were introduced to a lot of helpful information about the XM Cyber company and their services, which we would like to share with our audience.
An introduction of XM Cyber features and Attack Path Management Platform. -Where does the innovation stand?
XM Cyber is a leading hybrid cloud security company changing how innovative organizations approach cyber risk. By continuously uncovering hidden attack paths to businesses’ critical assets and security control gaps across cloud and on-prem environments, it enables security teams to remediate exposures at key junctures and eradicate risk with a fraction of the effort. Many of the world’s largest, most complex organizations choose XM Cyber to help eradicate the risk.
A chain of attack vectors (vulnerabilities, misconfigurations, user privileges, human errors, etc.) that enables lateral movement through an organization’s network is called an attack path. Once an attacker is inside the network, they can move laterally, escalating their privileges and targeting systems to gain access to sensitive data and business-critical resources. They can access the cloud environment by moving from a compromised enterprise AD user to the associated Azure AD user.
Our platform uncovers and visualizes every possible path an attacker can take to reach an organization’s critical assets, enabling the security team to remediate in advance before a devastating attack occurs.
XM Cyber Goals and Main Objectives
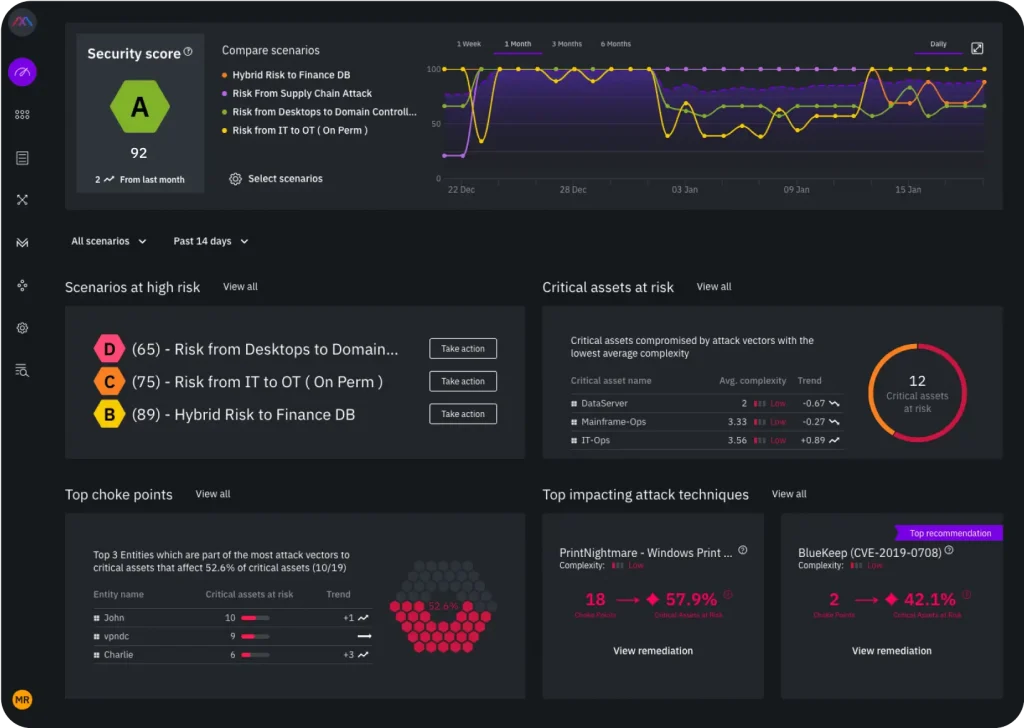
It provides guidance on where to direct resources to remediate the most damaging attack paths first, along with prioritized, step-by-step instructions allowing organizations to spot attacks before they happen and close gaps in their security controls before they are exploited. The risk quantification will enable users to quantify risk easily, see security posture improvement trends over time due to continuous hygiene improvements, and see the value derived from new security investments. With an accurate, real-time security score that’s easily understood, security leaders can drive better business decisions and report the absolute risk of the business to the board, finally answering the question: is our business secure?
With XM Cyber’s Attack Path Management platform, security teams are no longer bombarded by security alerts that they do not know how to prioritize. Instead, they are provided with complete visibility into all threats to their critical assets, a continuous view of their security control gaps, and automated compliance validation and reporting for key standards like ISO, NIST, GDPR, SWIFT, and PCI, amongst others. This saves businesses time and money and further boosts their overall security posture, making them less prone to costly breaches that can lead to loss of revenue and reputation.
The implementation of the platform into the everyday processes of companies
We are a SaaS platform that can continuously see your hybrid network through the eyes of an attacker and spot attacks before they happen. Safely run attack modeling across your infrastructure to identify misconfigurations, vulnerabilities, and overly permissive identities to pinpoint and remediate high-risk exposures quickly. Connect via APIs or lightweight sensors if the organization is self-hosted (on-prem) to calculate different attack vectors and uncover exposures that critical risk assets, such as privilege escalations, access token theft, and more.
With the XM Cyber, you can quickly identify the security gaps that enable attackers to move laterally within the network and prioritize based on risk to critical assets and impact on business; and know what to fix first to stop attacks in the making.
An in-depth real case analysis on how XM Cyberattack simulations are performed
XM Cyber’s graph-based simulation technology continuously discovers the attack paths that lead to critical assets, enabling complete visibility into organizational security posture. This allows users to understand how vulnerabilities, misconfigurations, user privileges, etc. chain together to create a cyberattack path that jeopardizes critical assets. At XM Cyber, we determine the likelihood of compromise to a critical asset by two main factors: the attack’s complexity and how many hops it takes an attacker to get to your critical assets. We analyze attack paths and calculate the actual risk by combining the complexity and the number of hops it takes to put critical assets at risk.
The complexity of an attack path across entities is determined by many factors, including what prerequisites are required, how long it takes, what access is needed, and how many steps are needed for the attacker to get from the breach point to your critical asset. At each step in the path, the attacker uses a technique to compromise the entity and uses that entity to step to the following entity in the path on its way to the target.
Attack Path Management
Most of our assets can be compromised – without knowing where to look, we are blind. Before the emergence of attack path management, there was no efficient way to identify and break the critical points in the attack chain. To do that, you need a clear view into the entirety of your environment from the eyes of an attacker. It is not enough that you are just monitoring the threats and alerts; it’s about understanding the context of these vulnerabilities within your environment and the attack paths that these vulnerabilities offer to an attacker looking to breach your critical assets. This is achieved through a deep analysis of the environment, and only then can we define the steps needed to eradicate, or at least mitigate, the risk to our organizations.
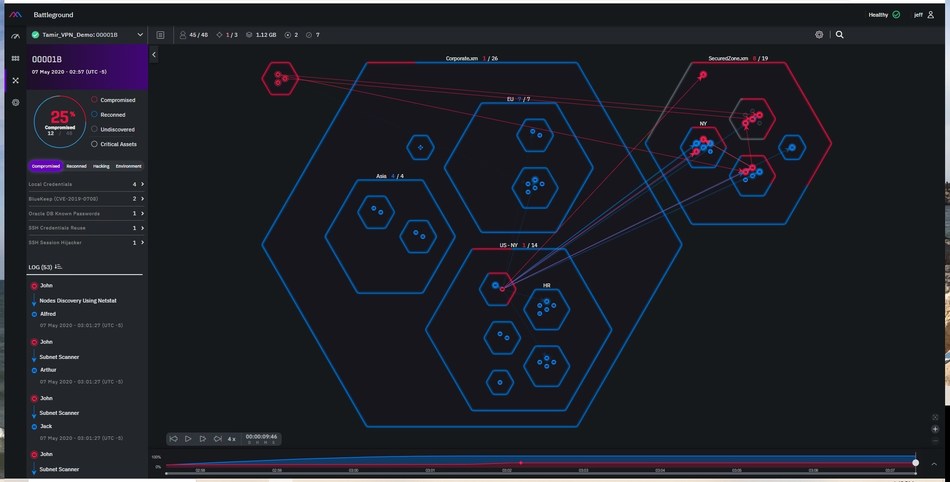
An example would be an attacker infiltrating an enterprise environment by sending phishing mail that executes code using a vulnerability on an unpatched machine when opened. The next step for the attacker would be to exploit the compromised AD user’s local and domain credentials through credential dumping techniques. This user has permission to add themselves to an AD group, so the attacker can now add the compromised AD user to an AD helpdesk group. The helpdesk group has the AD permissions to reset other users’ passwords, and now the attacker can reset a password to another user, preferably an old, out-of-use admin.
Now that they are an admin, they can do many harmful activities in the network – for example, the attacker can run malicious code by adding a script login to other users in AD. Every time a user logs on, the script will run, and the attacker can gain access to other computers and conceal his lateral movement for a long and persistent presence in the network.
With the privileges of being a domain admin, they can access your business-critical assets such as the exchange server, financial data, production servers, etc. If this compromise wasn’t of concern enough, the attacker has access to all the users in the domain and can locate users that have an Azure access token stored on their machine. This way, he can use it to connect to the Azure environment and continue compromising critical assets. The quick progress towards being a domain admin can facilitate a quick takeover of your critical assets for ransomware.
Main challenges that XM Cyber faced along the way
Key business outcomes that are gained through XM Cyber include:
- Resource efficiencies are due to the focus on chokepoints (the key junctures where attack paths converge). By directing resources to remediate the choke points, users can cut off an attacker’s way to business-critical assets with the most efficient use of time and resources and the most significant impact on risk reduction.
- Return on security investment – With a single comprehensive view of all hidden attack paths across the hybrid network, security teams know how effective their protective measures and processes are in securing the business and can thus continuously improve them.
- Time to value – Users can conduct automated, continuous risk reduction that’s safe, scalable, and simple to deploy to gain security posture visibility immediately upon deployment, whenever there are changes within a dynamic environment, and whenever new security tools are deployed.
The ultimate benefit of getting the XM CyberAttack Path Management platform
With XM CyberAttack Path Management platform, security teams are no longer bombarded by security alerts that they do not know how to prioritize. Instead, they are provided complete visibility of all critical assets’ threats. This saves businesses time and money and further boosts their overall security posture, making them less prone to costly breaches that can lead to loss of revenue.



