What is Identity and Access Management?
One of the most important sectors in Cyber Security field is that of IAM. Identity access management is a fundamental and critical cyber security capability, to ensure the right people and things have the right access to the right resources at the right time.
Identity and Access Management (IAM), in business terms, refers to the management of roles and access privileges to individuals. These individuals can be your employees, customers, or any freelancers.
The main purpose of Identity and Access Management is to ascertain the digital identity of these individuals. The ultimate purpose is to manage the access lifecycle. The following concepts is the key for the IAM.
IAM Domains:
1.Identification, Authentication, Authorization, and Accounting(IAAA)
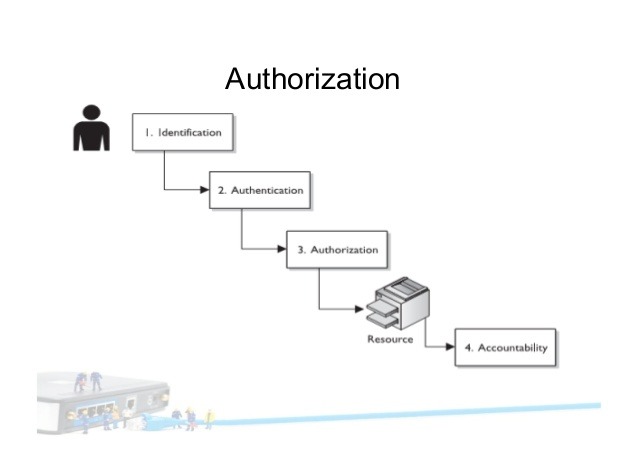
Identification: Who are you? Your Name, username, ID number, employee number etc.
Authentication: Is the process of verifying the source of the presented data. The entity could be a user, process, or device. When we log on to our systems in the morning, we enter the username and password. Authentication is often confused with authorization even though they are distinct technologies and practices. In some computing models, authentication and authorization are blended together and have little distinction or separation in implementation or management.
Apple iOS, Android, for example, uses biometrics for both authorization and authentication, and the end-user experience is blurred regardless of the action type. By definition, authentication is a login (username) in addition to some form of secret, historically a password, to establish proof or trust in an identity. It is essentially a validation of who you say you are.
Authentication of your identity = login + shared secret (password)
While there are countless variations of shared secrets that can be used within a login, such as pin codes, passwords, keys, two-factor authentication, and so on, the login itself is generally not a secret and often guessable for an identity. For example, login could be “jtitor” for my alias as an abbreviation of John Titor’s name. However, a login could also be something more complex like an employee number, which better masks a user’s identity. For highly secure environments, this second approach is preferable, especially for administrator or root accounts. You do not visually identify the privileges with the account simply by looking at the account or username. Obscurity is not security but it often helps!
So, in simple terms, authentication is nothing more than proving your identity or your ownership of a given account. It does not provide permissions, privileges, or access, just confirmation that you are who you say you are.
Authorization: Authorization is the next step after authentication. You cannot be authorized to perform a function, have privileges assigned, or even perform tasks in a given role, without some form of authentication happening first. Essentially, is the process of granting access rights (entitlements) to a user, program, or process. Authorization determines “what we can do” within a target resource.
Accounting: As mentioned, many different roles, applications, groups need accounts. Someone with an account payable business role, for example, will always need to have read and write access to the accounting system. The required relationship is defined by the relationship type that links together the business role and the IT role that contains the entitlement definitions.
2.Priviliged Access Management(PAM).
Many multinational companies, large organizations operate hundreds or thousands of servers, databases, virtual machines, network devices (e.g. routers, switches, and firewalls), scripts and applications, all controlled and managed by a variety of privileged identities, also referred to as “privileged accounts.”
3.Identity Governance and Administration(IGA).
In many cases, a given organization may already have a tool that provides some degree of visibility and control over the account management process. You just need to leverage that tool in the initial visibility process.
The critical first part of an overall Identity Governance process is enabling and maintaining visibility over the “current state”. This requires integration with authoritative sources of identity, connectivity to target applications where the accounts and access control resides, and the building of something we call an entitlement catalog.
4.Data Governance and Protection.
In this digital world, data governance is not something simple. Is critical for the successful business operations. Is a term used to describe the overall, comprehensive process for controlling the integrity, use, availability, usability, and security of all data owned by or controlled by an enterprise.
Governance provides standards and policies that allow us to harmonize resources and provide transparency for legal compliance.



