Cuckoo Sandbox: Created by Claudio Guarnieri during the 2001 Summer of Code, the community has embraced it as one of the best digital forensics tools. In large part, this is due to its modular structure. As an open-source program, developers around the world are free to work with it, as it has exponentially increased functionality and allows the software to accept modifications in the ever-changing world of Internet security.
Cuckoo Sandbox works effectively with Android, Windows, Linux, and iOS systems and automates the process of dealing with malware. Companies worldwide are starting to integrate it into their servers’ front, and back ends, and a big reason for that is how easy it is to integrate.
Cuckoo sandbox is an automated analysis system of open-source malware. It is used to automatically run and analyze files and collect comprehensive results describing what the malware does while running on an isolated operating system.
It can retrieve the following type of results:
- Malware Analysis | Security Evaluation for Android Applications
- Traces of calls executed by all processes created by the malware.
- Files created, deleted, and uploaded by the malicious software during its execution.
- Memory spaces of malware processes.
- Monitor network traffic in PCAP format.
- Screenshots were taken during the execution of the malware.
In addition, it supports the use of signatures for better analysis of malware and the interface with a virtual machine to be used as a sandbox to carry out the necessary processes and controls.
Conditions of Operation
- Install oracle virtual machine or VMware
- Install operating systems according to virus and vulnerability analysis to create a lab.
- Installation of the viruses or files to be analyzed depending on the case
- There is the possibility for static and dynamic analysis, and in some cases, it is possible to monitor and analyze the behavior of a virus.
Use Cases with Cuckoo Sandbox
Cuckoo is designed to be used both as a standalone application and to be integrated into larger frameworks, thanks to its highly modular design.
It can be used to analyze the following:
Generic Windows executables
- DLL files
- PDF documents
- Microsoft Office documents
- URLs and HTML files
- PHP scripts
- CPL files
- Visual Basic (VB) scripts
- ZIP files
- Java JAR
- Python files
- Almost anything else
Thanks to its modularity and powerful scripting capabilities, there’s no limit to what you can achieve with Cuckoo.
How Cuckoo Sandbox works
The analysis process starts when a file is submitted to Cuckoo. The information sent to Cuckoo is initially stored in an internal database (SQLite or MySQL), and when a virtual machine is available, the analysis process begins. Before uploading the file from the respective analyzer, the virtual machine returns to its original state (clean state) through the restore snapshot process. Essentially, the only software running on the virtual machine for the analysis process is the Cuckoo Agent. This program is a server that receives the analysis information and passes it to the analyzer.
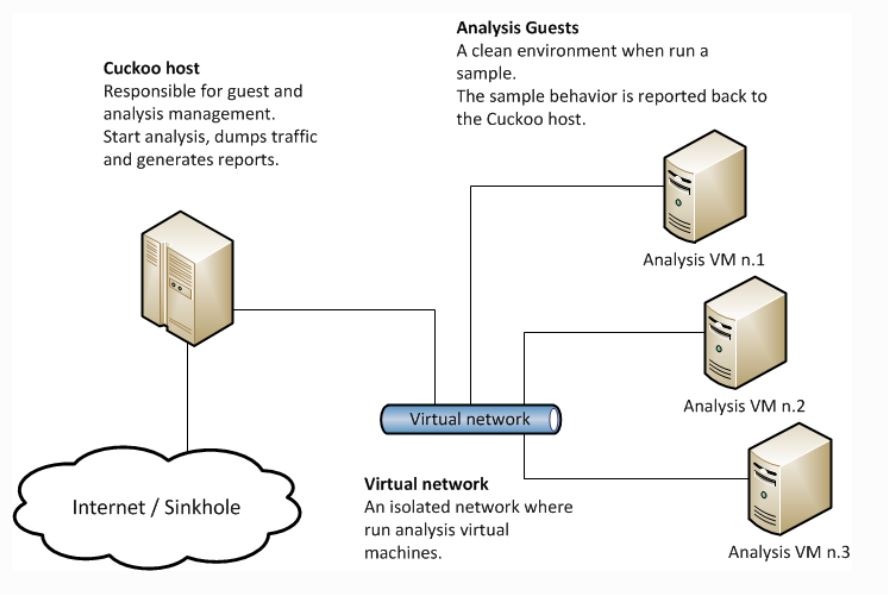
The analysis packages (analyzers) of Cuckoo determine the way in which the respective file is executed in the virtual machine. For each format, the corresponding analyzer is used.
In addition to the main classes of Cuckoo, there are also some auxiliary classes. These classes run concurrently with the analysis process and do not provide any information about the virus.
The main function of Cuckoo is based on the cuckoomon dynamic library, which records all the actions performed when starting a process in the virtual machine. The function of this library differs for each file execution so that it is not detected by execution protection mechanisms in a restricted environment (anti-sandbox). For each function that is analyzed when running files in the virtual machine, the cuckoomon library takes care of logging the resulting data. This is achieved through API call parsing processes at the user level.
As soon as the execution of a file is completed, the processing classes (processing modules) are activated.
The processing classes collect all the data resulting from the file’s execution, such as processes, data behavior, API calls, etc. This information is then forwarded to the enabled detection classes to detect malicious or suspicious behavior.
Upon completion of execution of the processing classes, the reporting procedures (reporting modules). All elements are already stored in an internal database, and now, depending on the reference class to be used, Cuckoo can give us reports in HTML and JSON format. In addition to generating reports, we can also generate automated signature alerts. Triggering of these alerts is done based on criteria set in the analy.



