The infamous cyberattack that happened in Albania at the beginning of summer took every IT professional’s attention based on the attack’s nature. In July of this year, the Albanian government suffered a major cyberattack, resulting in websites and services becoming unavailable and much confidential information being exposed to the public eye. To help investigate this attack, Microsoft played a crucial part in conducting the security auditing of all impacted systems.
The Albanian cyberattack that became a study case
Microsoft assessed with high confidence that on July 15, 2022, actors sponsored by the Iranian government conducted a destructive cyberattack against the Albanian government, disrupting government websites and public services. At the same time, Microsoft Threat Intelligence Center (MSTIC) assessed that another Iranian group leaked sensitive information that had been exfiltrated a month before through different websites and social media. Also, a report published by the FBI and the Cybersecurity Infrastructure Security Agency (CISA) last Wednesday mentioned that Iranian attackers gained access to the Albanian system more than 14 months ago.
“An FBI investigation indicates Iranian state cyber actors acquired initial access to the victim’s network approximately 14 months before launching the [July] destructive cyberattack, which included a ransomware-style file encryptor and disk wiping malware,” the report says.
This type of cyberattack is very interesting according to its nature and has raised a few eyebrows among cyber and IT professionals worldwide. Here is a path of all the attacks in a storyline.
Iran’s cyberattacks timeline
- In May and June 2022, Iranian state cyber actors conducted lateral movements, network reconnaissance, and credential harvesting from Albanian government networks.
- In July 2022, the actors launched ransomware on the networks, leaving an anti-Mujahideen E-Khalq (MEK) message on desks. When network defenders identified and began to respond to the ransomware activity, the cyber actors deployed a version of ZeroCleare destructive malware.
- Homeland Justice created a website and multiple social media profiles to post anti-MEK messages in July 2022.
- On July 18, 2022, HomeLand Justice claimed credit for the cyberattack on Albanian government infrastructure.
- Homeland Justice posted videos of the cyberattack on their website on July 23, 2022.
- During the period from late July to mid-August 2022, HomeLand Justice social media accounts posted a poll asking for flagging information to be released by the government and then shared that information—either directly via a .zip file or a screen recording showing documents—as a result.
- In September 2022, Iranian cyber actors launched another round of cyberattacks against Albania, using the same TTPs and malware as the July cyberattacks. These were presumably carried out in retaliation for the country’s public attribution of those attacks and the severing diplomatic ties with Iran.

The technical aspect of the Albanian cyberattack
The forensics analysis conducted by Microsoft after gathering evidence resulted in these statements:
- The attackers were observed operating outside Iran
- Other known Iranian hackers previously used the tools used for operating the attacks
- Also, the wiper code was used by an Iranian hacker
- The ransomware was signed by the same digital certificate as other tools used by Iranian hackers
- The attacker has targeted other nations, sectors, and entities implicated with Iran’s interests.
The well thought the attack had multiple stages, which Microsoft divided into Initial Intrusion, Data exfiltration, and Data encryption and Destruction.
Initial Intrusion: The timeframe thought to be of the attack is 14 months before the initial threat. The initial access to Albanian government systems was obtained after exploiting a CVE of Microsoft SharePoint component unpatched (CVE- 2019-0604) in early May and gained access in July using a misconfigured service account of a local administrative group member. At this moment, the attackers used the compromised account to create new exchange accounts and add them to the Organization Management role group, according to the CISA report.
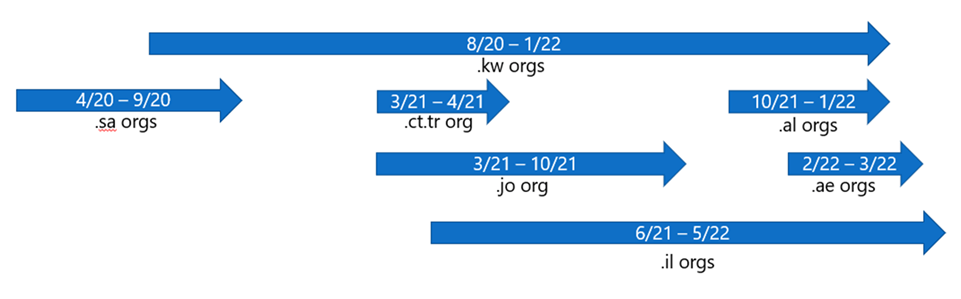
Data exfiltration: Through the analysis of exchange logs, it appeared that mail was exfiltrated from the victim’s network between October 2021 and May 2022. During this time, the attacker has been exfiltrating data from different organizations in countries such as Israel, Jordan, Kuwait, Turkey, Saudi Arabia, etc., that align with Iran’s interests. And a few months before the attack, the attackers connected to the victim’s organization’s VPN IP addresses, where they executed an “advanced port scanner.”
Data encryption and Destruction: This cyberattack used a different technique consisting of deploying ransomware first, and the deployment of wiper malware follows that. According to the CISA and FBI analysis report, the attacker logged into the victim’s organization print server via RDP and started encrypting all files in the target system, leaving behind a ransom note. At the same time, the hackers began a wiper attack that lasted almost 8 hours, which resulted in wiping disk drives. A separate and unknown Iranian actor subsequently performed the wiper attack.
Hackers hit Albania again
After all the commotion and troubles caused by these attacks, the Albanian Prime Minister announced on September 7 that Iran’s diplomats would be expelled from the country after the massive attacks in July.
“This is possibly the strongest public response to a cyberattack we have ever seen,” John Hultquist, Mandiant’s vice-president of intelligence, said following Albania’s announcement.
But a few days later, the hackers again hit the Albanian information systems. This time they targeted TIMs, the Traveler Information Management System. This caused queues at border points, where the registration of citizens and vehicles entering and leaving the country had to be done manually. Again, on September 19, the former Chief Police emails were released by the same “Homeland Justice” group, which is thought to be associated with the hacker group terrorizing the Albanian state. After all these issues, the NATO officials met with Albanian state representatives, who stated in a press conference that Albania has their full support and will help the government defend itself against these malicious activities. So far, it seems the attacks have quite down, but it is yet far to know if this cyber war has come to an end.