Lately, a fake windows 11 update has circulated the internet, which is risking the users’ safety. It is spreading malware that could steal a user’s personal information. The reason why this malicious software is making rounds is because of its nature of it, which is quite interesting and has raised some brows from security researchers. Researchers from CloudSEK have analyzed this scam and have shared the results with the rest of the world.
The attackers that created this fake update have managed to replicate the Window’s official website. It has a very inviting ‘Download Now’ button, that has scammed a lot of users globally. By clicking the download button, on the user’s PC, a 1.5 MB ZIP file is downloaded that contains the executable files inside.
According to researchers, this is a new form of malware, that they named ‘Inno Stealer’ due to its use of the Inno Setup Windows installer. The “Windows 11 setup” executable found inside the ISO when launched creates a temporary file named PN131.tmp, and another.TMP file that writes 3,078KB of data to the infected PC. CloudSEK researchers explained that this loader helps initiate new processes using the ‘Create Process Windows API’ which starts new processes and plants four files within the system.
Windows 11
The first two files are Windows commands that disable Registry security and add Defender exception, by even uninstalling some security products. The third file is a command that when executed, run with the highest system privileges. Meanwhile, the last file VBA script is required to run dfl.cmd (Windows domain functional level). This marks the ending of the first stage of the infection. Meanwhile, the second one begins in which another file with an SCR extension is dropped inside the User’s- App Data directory of the system. This file contains the malicious payload which begins the execution ready to steal information from the victim’s personal computer.
Inno Stealer
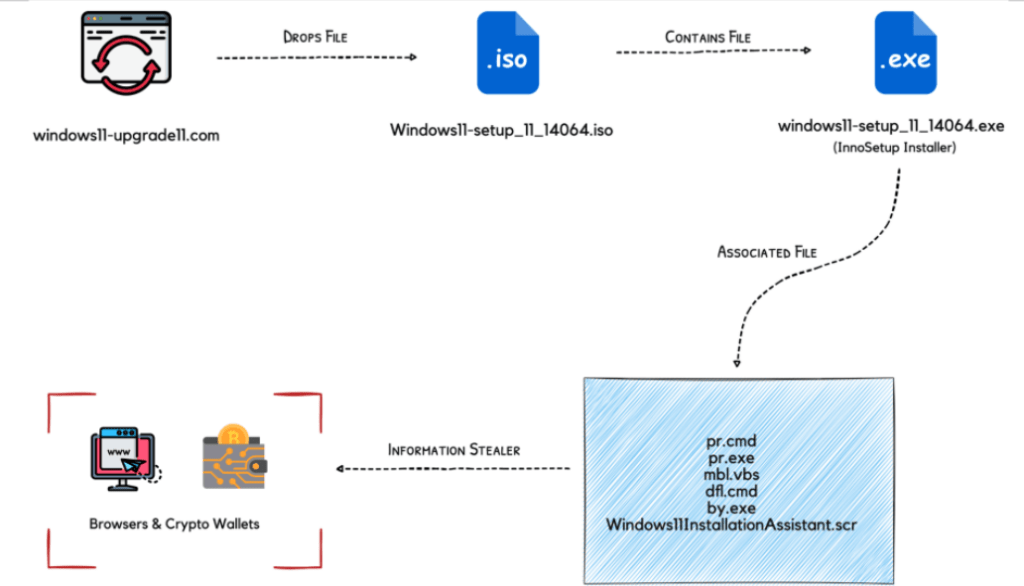
The Inno Stealer targets browsers and crypto wallets, which includes stealing web browser cookies and storing information in crypto wallets in different file systems. This malware can even attack the biggest browsers in the world like Chrome, Edge, Opera, etc. One interesting thing about the Inno Stealer is that it also has additional payloads that can be executed possibly during the nighttime when the victim is not in front of the PC.
Overall, this situation has caused a lot of commotion, where the users are frightened about their security. We must say that this is not the first time that a similar situation has been reported. Microsoft has been attacked in ways like this even before. But this time this issue seems to be more complex, where the user is being deceived daily. Therefore, it is recommended that we must download updates from within our control panel, or from the official resources, but never from third-party resources. If the update is not available right away, we mustn’t hurry to get the update manually and causing the raise of the security risks that may come with it.



